Cyber threats training module | Cyber safety training - NAB
Cyber threats training module
Welcome to our Cyber Threats training module for small and medium sized business owners and staff.
The average self-reported cost of cybercrime for small businesses rose to $49,600 in 2024 compared to the previous financial year of $45,965, up by 8%.
According to the Australian Bureau of Statistics in 2022 to 2023, 91.9% of businesses had turnover of less than $2 million.
In this module you will learn:
- How to identify cyber threats including malware, ransomware, business email compromise (BEC) and invoice scams
- Best ways to protect yourself and your business from cyber threats
- Where you can go for help and more information
-
What is Malware?
Malware is short for ‘malicious software’. Cyber criminals use malware to make your computer malfunction, cause damage, disrupt you or steal your information for financial gain. Your computer can become infected with malware in many ways; when you download software, share files, click on links on emails, or insert USB drives, to name a few.
Common types of malware are:
- Keylogger – this monitors everything you type on your keyboard in order to steal passwords or credit card details.
- Spyware – this is a program designed to secretly allow someone to spy on what you do on your computer.
- Trojan – this let criminals access your systems and information without your knowledge.
- Ransomware – this locks all your files and then asks you to pay a ransom to unlock them.
How can I tell if I'm a victim of malware?
Some of the signs your computer is infected with malware are:
- It takes longer than normal to start and is running slowly
- New and unfamiliar icons appear on your desktop or browser
- It keeps crashing.
Keep in mind some types of malware especially, keyloggers and Trojans, are very difficult to identify.
How can you help protect your business from Malware?
- Keep your software up to date. Malware is always changing. Criminals get smarter and more innovative every day, so ensure you set automatic software updates.
- Use anti-virus software. Install a reputable anti-virus program and keep it up to date. Never rely on trial version, because they quickly go out of date.
- Create backups. Put in place procedures to regularly (or automatically) backup (copy) your important files. You should do this on a separate device to your computer, such as a USB memory stick, portable hard drive or CD, or secure cloud-based storage.
- Educate your employees to recognise suspicious messages. Criminals often send malware in the disguise of links or attachments in emails or text messages.
Check your understanding
No. Sounds like her computer is just old and needs to be replaced.
Incorrect. The combination of a blank email attachment and her laptop running slowly suggests that she’s the victim of a malware attack. Cyber criminals often create email addresses that look similar to legitimate email addresses to trick the recipient into opening malicious links and attachments. Always check the email is from a legitimate source before you click.
Yes, there is a strong chance she has malware on her computer.
Correct. The combination of a blank email attachment and her laptop running slowly suggests that she’s the victim of a malware attack. Cyber criminals often create email addresses that look similar to a legitimate email addresses to trick the recipient into opening malicious links and attachments. Always check the email is from a legitimate source before you click.
-
What is Ransomware?
Ransomware is a type of malicious software that locks the files on your device so you can’t open them. A message (or ransom note) from the criminal will appear on your screen, demanding money in return for a code to unlock the files.
You can become a victim of ransomware by accidentally by clicking on an email attachment, or if your security software isn’t up to date.
Cybercriminals usually demand you pay the ransom in a virtual currency, such as Bitcoin, because it’s difficult for police to trace.
Ransomware attacks are just like any other extortion attempt. The police advise that businesses should never comply with a criminals’ request for money.
How can you help protect your business from Ransomware?
- Be wary of unsolicited messages and train your employees how to spot suspicious emails.
- Always keep your operating system, anti-virus and applications up-to-date.
- Back up your data. You should save a copy of your important files onto a removable hard drive, USB drive or secure cloud storage. If you back up to a physical device, always disconnect it from the computer when it’s done, because cyber criminals can encrypt or delete back-ups if they’re connected to the computer or network.
- Test that your back-ups work correctly by regularly restoring your data to a separate ‘test’ location.
- Put in place incident management plan that has key contacts, processes and business continuity plans in case you do have an issue.
Check your understanding
Use strong passwords and a different one for every account.
Incorrect. This is good cyber security practice, but it won’t stop a ransomware attack because they come through phishing emails or from weaknesses in an out-dated operating system.
Keep your operating system and anti-virus software up-to-date.
Correct. Keeping your anti-virus software and operating systems up-to-date will help stop cyber criminals.
Back up your data on a separate device or in the cloud.
Partially correct. This is an excellent practice and will help you recover your data after a ransomware attack, but it won’t prevent one. The best way to protect your business is to keep you operating system and anti-virus up to date, and to not click on links or attachments in suspicious looking emails.
-
What is Business email compromise (BEC)?
A BEC is an email that appears to come from someone senior in your business, and urgently asks you to do something like make a payment or transfer funds. Also known as ‘CEO phishing’, the email address may look like it’s from your managing director, chief executive officer or chief financial officer. Criminals hope the urgent tone and the apparent seniority of the sender will make you act without checking the request is real.
A BEC email could be sent from:
- a simple email address such as ‘iamceo1@gmail.com’
- an email address very similar to a senior business person, for example john@s1ight.com.au instead of john@slight.com.au
- what appears to be a correct email address, but if you reply the email goes to a different address
- the impersonated sender’s real email address, which happens if a criminal has stolen the email credentials from a previous phishing email, or with malicious software.
For example:
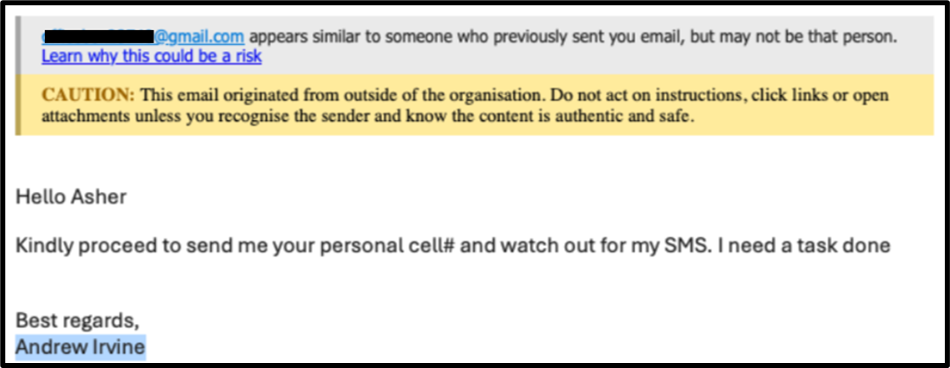
How to help protect your business from BEC emails
Read the 4 tips below, and then check your understanding with our questions.
1. Create a safe payment process. Create a process where people responsible for making payments must carefully check a requester’s email address, and call to confirm the request is real using the contact details they have on file.
2. Use multi factor authentication (MFA). This means adding an extra authentication method in order to access a system, such as a code sent to your mobile phone via SMS. This means that even if someone steals or guesses your password, they will not be able to get into your account because they will not have the 2FA code.
3. Create a confirmation process. Create a process to confirm any unexpected requests for payments from Senior managers
4. Raise awareness. Help your employees understand more about the tricks and scams of fraudsters. If your business gets a BEC phishing email or a fake invoice, safely share it around so your employees know what to look out for.
Check your understanding
Carl is a financial assistant in a small business. He receives an unexpected email from the owner of the business. It reads:
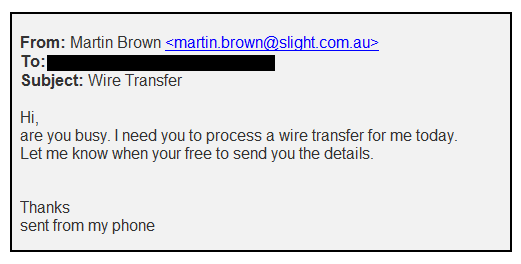
He should reply and ask the sender for more information.
Incorrect. He shouldn’t reply, because if the email is fraudulent, he will be replying to the criminal. He should phone Martin to check the email is real, using the contact details he has on file.
Phone to verify the email is real using a contact number for Martin that he has on file.
Correct. Always phone to check an email like this is legitimate, and make sure you use the contact details you have on file, not the ones in the email itself, which will most likely be fake.
-
What is an Invoice scam?
This is when a business receives an emailed invoice from a supplier whose email account has been compromised by a criminal. The criminal will use the supplier’s real invoice, and simply change the bank account details to their own. Because the invoice looks legitimate, often the business doesn’t question the change in the bank details, and sends the payment to the criminal’s account.
A variation of this scam is when a business gets an email from a criminal pretending to be a supplier, asking to cancel a recent payment, and make the payment to a new account.
How to protect your business from invoice scams
1. Create a safe payment process. Create a process where the person who pays invoices has to carefully check the payee’s banking details. If there has been a change, call the payee to confirm the change is legitimate, using the contact details you have on file.
2. Raise awareness. Help your employees understand more about the tricks and scams of fraudsters. If your business gets a CEO phishing email or a fake invoice, share it around so your employees know what to look out for in the future.
Reply to the email to verify the change.
Incorrect. You should never check the request is real by emailing or calling using contact details listed on the email. If the request is fraudulent you will be contacting the criminal directly.
Update the payment details for this supplier.
Incorrect. You should always check a change to payment details by phoning the person using a number you have already on file, not what may be listed on the email.
Contact the sender to verify the change using a phone number that you already have on file.
Correct. You should always verify a change to a supplier's payment details by phoning them on a number you already have on file.
Congratulations!
You have completed NAB's Cyber Safety module on Protecting your business against cyber threats. We hope you found it valuable.
Test your knowledge on other cyber safety topics.
Important information
Apologies but the Important Information section you are trying to view is not displaying properly at the moment. Please refresh the page or try again later.

