Spam and phishing emails | Tips to identify them - NAB
Protecting yourself
We can all play a part in preventing cybercrime. The first step is learning to identify suspicious messages.
Identifying and managing spam
Spam refers to unsolicited junk emails that are sent to large numbers of people at once. Spam emails are typically advertising fake products or get rich quick schemes.
Don’t bother unsubscribing from spam emails; this just confirms to spammers that your email address works and that they should keep spamming you.
The most effective way of managing spam emails is to use your email settings to send these emails to your junk folder.
What is phishing?
Phishing (pronounced fishing) emails are more sinister than spam. They’re designed to trick you into providing personal information like:
- a mobile phone number
- usernames and passwords
- credit card details or bank details.
You’re in control with phishing emails
Criminals use email for the same reason legitimate business do, it’s a cheap way to get to a lot of people.
The phishing email you receive was probably sent to several thousand other people as well. You have the opportunity to outsmart these criminals by taking a few seconds to look for the signs that something is up.
Phishing emails often pretend to be from legitimate companies such as banks, courier companies, or government departments, and can contain links to fake websites or ask you to call an unofficial number.
These fake sites look very similar to the real ones, including ours, and are designed to trick people into entering their bank details.
Our Security team monitor the Internet for fake NAB websites and request to have them removed from the Internet to protect our customers.
Sometimes the emails will have an attachment that appears to be an invoice, or document. When you try to open the attachment, it installs malware on to your computer without your knowledge.
Using the example above, here are a few signs the email you received may be a phishing email.
Sender address
This might be unusual, misspelled or slightly different from the correct address, for example nab.com instead of nab.com.au.
Generic greetings and sign offs
Phishing emails are sent out to hundreds of people at once so use generic greetings and sign-offs.
Poor grammar and spelling
This can be a tell-tale sign, but it isn’t always the case. Remember, criminals can use spell check too.
Creating a sense of urgency
Phishing emails will often encourage you to click a link or download an attachment to avoid a problem to create a sense of urgency. Always read an email carefully before taking any action.
Suspicious links and fake websites
If you receive an email with a suspicious link, hover over the link with your mouse to see the actual web address the link leads to – it could lead to a fake website.
Malicious attachment
Often an attachment will appear to be a PDF, image or Office file, but when you try to open the document, it tries to run a program or script intended to infect your computer with malicious software.
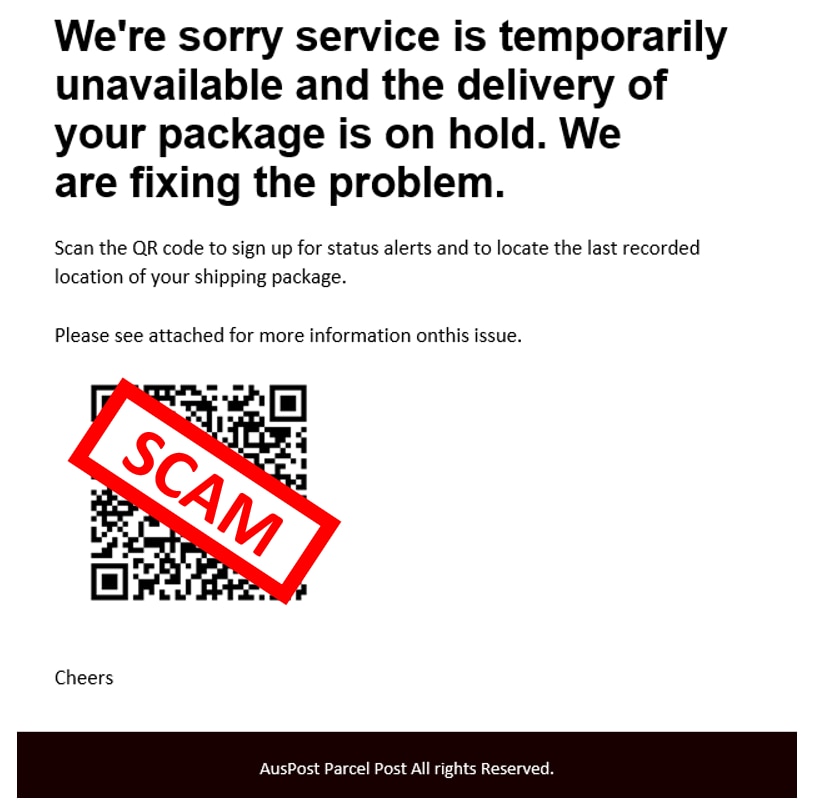
QR code phishing (‘Quishing’)
Criminals are increasingly using QR codes in phishing messages, as they may bypass email spam filters designed to detect malicious content. When scanned by a mobile phone, the QR code image will open a website which may contain malware, or a phishing site designed to encourage people to provide personal details.
Here’s an example:
SMS phishing
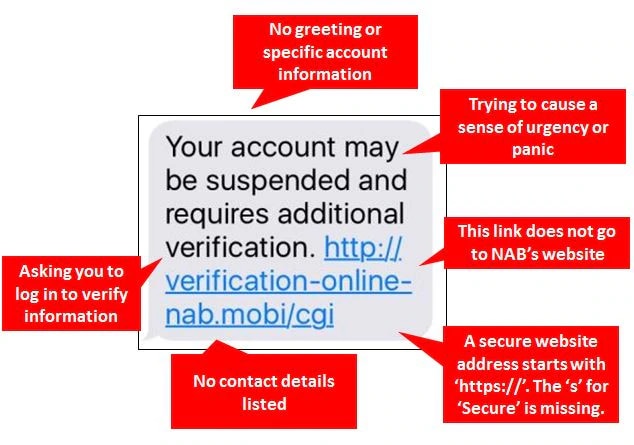
It’s not just email anymore. Cyber criminals are using other channels like SMS to conduct phishing. These fraudulent text messages use the same tactics as phishing emails, often pretending to come from a legitimate company.
Because text messages seem more personal, these messages are often not questioned in the same way as suspicious emails. Criminals are able to set the sender name of an SMS to anything they like. It’s the same as when you send a letter in the post; you can write whatever sender address you like on the back – it doesn’t have to be your real name or address. Sometimes criminals set the sender name as “NAB”, meaning that malicious SMS messages can appear in the same message thread as legitimate SMS messages.
Please see an example below.
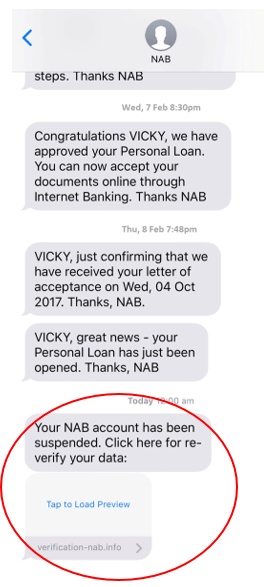
This can be confusing - but trust your gut. NAB will never “suspend your account”, or send you a link to “verify your identity”. These messages are not a sign that NAB systems have been breached in any way– it simply means a criminal is impersonating our brand.
Always stop and think before clicking on a link in an SMS.
File sharing phishing
Increased use of file-sharing services such as Dropbox, Google Drive and OneDrive has led to an increase in fake emails pretending to be links to documents.
In reality, these emails contain links to lookalike file-sharing websites designed to steal your credentials, or download malicious software on to your computer.
Bank Impersonation Scams
Bank impersonation scams involve criminals tricking you into handing over your money or personal details by pretending to be someone else. Criminals often impersonate trusted sources through fake calls, texts, social media ads or emails. They create a false sense of urgency to pressure you into acting quickly.
Download Spot the red flags of impersonation scams (PDF, 222KB) to learn more.
Digital wallet scams
Digital wallets are a fast, secure and easy way to make payments on the go, online or in store. They securely store a digital version of your payment card on your phone or device to make purchases, without the need to carry a physical card.
A digital wallet scam often starts when criminals send customers phishing emails or text messages requesting personal and banking information or deliver malware to your device to steal this information. If you provide your payment card details in response to the phishing message (or phone call), criminals might try to add your payment card to a digital wallet in their control in order to make payments.
How to avoid digital wallet scams
- If someone tries to add your payment card to their digital wallet, you’ll receive an SMS or NAB app notification with a one-time security code to add your card to a digital wallet.
- Read the message containing the code carefully, and do not provide this code to anyone, including NAB.
- your card from unauthorised use by reading messages and emails carefully before clicking on any links or providing your banking details.
- Keep your physical cards secure at all times.
- Keep your devices with your digital wallet secure at all times.
- Where possible, it’s best to pay for things online via the organisation’s official website than over the phone.
- Contact the merchant through their official website or number to confirm payments
What to do if you get 'phished'
If you suspect an email or text message, don't respond to requests for information and don’t click on any links or open attachments, even if there’s a sense of urgency.
If you receive a suspicious email or text message pretending to be from us, report it immediately to phish@nab.com.au.
As soon as we identify new scams and phishing activity, we publish warnings and examples on our website so you know what to look for.
Report fraud
Learn how to identify if you’ve been affected by fraud or scams, what you can do immediately or how to contact us to report suspected fraud.
Helpful resources
Australian Government | Australian Cyber Security Centre (ACSC)
The Australian Cyber Security Centre (ACSC) brings cyber security capabilities from across the Australian Government together in a single location. It’s the hub for private and public sector collaboration and information sharing to combat cyber security threats. ACSC provides topical, relevant and timely information on how home internet users and small businesses can protect themselves from, and reduce the risk of, cyber security threats such as software vulnerabilities, online scams, malicious activities and risky online behaviours.
Learn more about the Australian Cyber Security Centre
Australian Government | ReportCyber
ReportCyber is a secure reporting and referral service for cybercrime and online incidents which may be in breach of Australian law. The ReportCyber website provides a cybercrime reporting mechanism as well as helpful information about cybercrime.
Australian Competition and Consumer Commission | Scamwatch
Scamwatch provides information to consumers and small businesses about how to recognise, avoid and report scams using publications, videos and other online resources.
Australian Government | Office of the eSafety Commissioner
The Office of the eSafety Commissioner provides online safety education for Australian children and young people, a complaints service for young Australians who experience serious cyberbullying, and address illegal online content.
Learn more about the Office of the eSafety Commissioner
Australian Government | Attorney-General’s Department
The Attorney-General’s Department website provides helpful information and resources about your rights and protections in regards to identity security, freedom of information and cyber security. The Department has developed a range of resources to assist people protect their identity and recover from the effects of identity crime.
Related articles
Easy ways to protect your computer from malware
Don’t be a victim of cyber criminals. Learn how to protect your computer from malware.
Handy tips for secure online shopping and banking
Stay in control of who accesses your information when browsing online with these simple tips.
How to spot scam phone calls
Learn how to recognise scam calls and keep your details safe when on the phone.
Important information
Apologies but the Important Information section you are trying to view is not displaying properly at the moment. Please refresh the page or try again later.




