Card and payment fraud | protect your business - NAB
Be on the alert to payment scams
Being able to accept payments by credit or debit card is essential for merchants in today’s world. Sadly, criminals are looking for ways to exploit these payment methods and commit fraud, whether it’s at the payment terminal or online.
It’s important to be alert to payment fraud and take steps to protect your business, otherwise you may be at risk of being left out of pocket for costly chargebacks and the value of fraudulently obtained goods and services.
We’ll look at some of the ways criminals try to deceive merchants by using stolen cards or setting up sophisticated scams to trick merchants into parting with their money.
Learn what to look out for with the NAB Security podcast on Merchant Fraud Risk and keep your business safe.
Fraudulent card transactions
There are two types of fraudulent card transaction- ‘card present’ and ‘card not present’. Different rules apply to how these fraudulent transactions are treated and who has the liability to pay back the value of the fraudulent transaction. These rules are set by the card schemes; Visa, Mastercard and American Express.
‘Card present’ fraud
A ‘Card present’ transaction occurs when the physical card is present at the time of payment. These include transactions where a PIN has been entered, or the physical card has been presented at the terminal eg Pay Pass or contactless transactions. In the case of a fraudulent transaction, this usually means that a legitimate customer’s card has been copied or stolen.
If a transaction is reported as fraudulent, the cardholder’s bank is liable to return the funds to the victim of the fraud - the genuine card owner.
‘Card not present’ fraud
‘Card not present’ fraud occurs when a transaction is processed without the physical card being present. In this scenario, the card details are provided over the phone, via email or an online payment channel. The card number, expiry and in the case of an online transaction the card verification number (3 digits at the back of the card) are provided to authorise the transaction. If a transaction is reported as fraudulent, the merchant holds the liability to return the funds to the victim of the fraud - the genuine card owner.
This process of returning funds is called a ‘chargeback’ and can be very costly to your business. There are security steps you can take to reduce the chances of accepting stolen card details.
What a fraudulent transaction may mean for your business
Even if a transaction is approved, and the funds settle into your account, the transaction may still be disputed as fraudulent. This can happen up to 120 days after the transaction has been honoured. For instance, if you have taken a booking for a hotel room for one night 3 months away, the applicable 120-day chargeback period only starts once the service has been provided. This means it only kicks in once your guest has stayed the night.
Many of these instances are covered in the Merchant Service Agreement.
Bin attacks
A BIN (Bank Identification Number) attack is when a fraudster attempts to determine if stolen card information can be used to make purchases. BIN attacks are common across online commerce. At NAB, we’re constantly improving our tools and systems to detect and reduce fraud, but it’s important our customers also remain alert about fraud.
Watch this video to learn more about the harmful effects of BIN attacks and what can be done about them.
Learn more about BIN attacks
Processing refunds
Refunds can be an opportunity for criminals to steal from your business. It’s important that you process any refund on the same card or device used for the original purchase. If anyone asks for a refund on a different card, politely ask them to return with the original card.
This is part of your Merchant Service Agreement, to help keep your business safe from fraud and scams.
Always check the card details to make sure you’re refunding the right card.
How to find the card details
If a card was tapped or swiped, make sure the card number matches the receipt. Check the EFTPOS terminal receipt to find the last four digits of the card number. If the receipt and the card number match you can process the refund.
If a payment was made by tap and go on a smartphone or smartwatch, a different card number is generated for each transaction. This means you need to check the device number to confirm you’re refunding the same device.
To find the device number, ask the customer to:
- open the digital wallet on their phone
- tap the circle with the three dots in the right hand corner
- look for Device Account Number on the screen.
Check that this device number matches the number on the receipt. If the numbers match you can process the refund.
Buy Now Pay Later refunds
If the original payment was made through Afterpay, PayPal or another Buy Now Pay Later service, you need to check the website of the service used. Each Buy Now Pay Later platform has its own refund process.
Terminal takeover
This is when a scammer physically takes over an EFTPOS machine and rekeys a transaction amount or pays for goods and services using a stolen card number. To do this they temporarily take physical possession or control of the EFTPOS machine. Terminal takeover is only possible when the manual keying function is left switched on.
In this scam, the details of a stolen card are manually entered or 'hand-keyed' into the EFTPOS machine by the criminal to make a significant purchase.
The scammer could also enter the details of a stolen card into the terminal and key in a purchase amount significantly larger than the original amount, then demand an immediate refund on another card.
You can see if a transaction has been 'hand-keyed' by the letter indicator in brackets as shown on the receipt below:
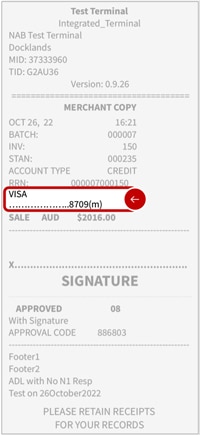
In the above example, the '(m)' displayed after the last 4 digits of a Visa card shows that the transaction was 'hand-keyed'. When refunding, make sure to always refund to the same card.
The below codes indicate the card payment method:
(c) Contact - applies to cards swiped and inserted.
(t) Tap - card was tapped.
(m) Manual entry - card details were hand-keyed.
(f) Technical fallback - the terminal was offline at the time of the transaction, and the transaction will be re-attempted at settlement.
Terminal theft
Terminal theft is where criminals steal the physical terminal from a business, often leaving a broken or fake terminal as a distraction technique. Criminals might attempt to process refunds to a card, tamper with the terminal in order to gather card information so that they can create counterfeit cards or capture PINs by adding a small camera to the terminal.
Third party payment scams
Convincing a business owner to accept a card payment and transfer funds to a third party is one way criminals try to access cash from stolen cards. It’s important to never accept credit card payments on behalf of anyone else.
An unfortunate example is that of a Sydney dance school owner. He accepted a credit card payment, via email, for children’s dance lessons ($700) as well as an additional amount of money ($500) to pay a driver who would drop the children at their lessons for the term. The owner processed the agreed payment of $1200. The next day, the driver arrived and collected his $500 in cash, but the children never showed up to the dance lessons, nor could the parents who booked the lesson be contacted. As it turned out, the card details had been stolen and the request for dance lessons and payment to a driver were part of a scam. The business owner was sadly responsible for the $1200 chargeback, as well as being out of pocket for the $500 he paid in cash to the driver.
Watch our video to learn more about how merchant scams can affect real people and their businesses.
Social engineering
Criminals may look for ways to gain access to your business systems to process payments for their own financial benefit. They may use manipulative or aggressive behaviour, often over the phone, to elicit password and other security information from a business. They might try to convince you to transfer funds, give them access to your computer or use information they know about you to send phishing emails or to conduct corporate espionage.
Tips to help safeguard your business from payment scams
Being alert to fraudulent payment activity can reduce the chances of your business falling victim to scams and suffering costly chargebacks and other financial loss. We’ve got some simple tips you can follow:
- Educate all front-line staff about fraud risks associated with your payment terminal and payment scams in general.
- Keep payment terminals behind the counter or on the person of your employees. Don’t allow customers to edit or manually enter transactions and if you don’t require the manual key entry feature on your terminal, ask your banker to switch it off.
- Always refund a transaction to the same card and remember to change your refund password regularly.
- Set a strong terminal password and activate the lock feature when the terminal is unattended.
- Keep a list of the terminals you have onsite, including their make, model and serial number. Do a daily check to confirm that the data matches.
- Do a physical check at the terminal, are there any changes or any evidence of tampering?
- Be cautious of customers who wish to correspond via email only and are not contactable by other means such as phone.
- Watch out for customers who claim to be not contactable and/or unable to view the goods being purchased.
- Beware of customers who are willing to pay more than the cost advertised or place unusually large orders for goods. If it sounds too good to be true, it usually is.
- Never accept payments on behalf of third parties or for services you didn’t provide.
- Don’t agree to forward payments or funds to other businesses or people.
- Be aware that if you accept transactions when the card is not present in the sale, it is you, the merchant, who is ultimately liable should a dispute be successfully raised against the transaction.
- Avoid any requests to transfer funds via Western Union.
- Trust your instinct – if you have concerns about a transaction, contact your bank for guidance.
If you’re a NAB customer and believe you’ve been impacted by a merchant scam, please contact us.
Helpful resources
For more information about protecting your business from fraud and payment scams, take a look at these helpful resources.
Australian Payments Network
As the self-regulatory body for payments, Australian Payments Network plays an important role in the governance of payment systems. They have useful resources relating to payment fraud including statistics and reports.
Australian Government | Australian Cyber Security Centre
The Australian Cyber Security Centre (ACSC) brings cyber security capabilities from across the Australian Government together. It’s the hub for collaboration and information sharing to combat cyber security threats. ACSC provides timely information on how home internet users and small businesses can protect themselves from cyber security threats. They also help users reduce their risks of software vulnerabilities, online scams, malicious activities, and risky online behaviours.
Australian Cyber Security Centre
Australian Government | ReportCyber
ReportCyber is a secure reporting and referral service for cybercrime. These online incidents may be in breach of Australian law. The ReportCyber website provides a cybercrime reporting mechanism as well as helpful information about cybercrime.
Australian Competition and Consumer Commission | Scamwatch
Scamwatch provides information to consumers and small businesses about how to recognise, avoid and report scams.
Australian Government | Office of the eSafety Commissioner
The Office of the eSafety Commissioner provides online safety education for Australian children and young people. It’s also a complaints service for young Australians who experience serious cyberbullying and addresses illegal online content.
Office of the eSafety Commissioner
Australian Government | Attorney-General’s Department
The Attorney-General’s Department provides helpful information and resources about your rights and protections regarding identity security, freedom of information and cyber security. The Department has developed a range of resources to assist people protect their identity and recover from the effects of identity crime.
NAB also partner with Forter and Ethoca, fraud prevention companies.
Related articles
Building employee awareness of cyber safety
Empower your employees to help manage your online security risks
Understanding the value of your business data
Protecting valuable business data from cyber crime is everyone’s business.
How to protect your website from being compromised
Learn how to protect your website against online attacks.
Important information
Apologies but the Important Information section you are trying to view is not displaying properly at the moment. Please refresh the page or try again later.




